The way to take away Trojan:Win32/Reqletter? Trojan:Win32/Reqletter is a virus file that infects computer systems. Trojan:Win32/Reqletter takes over the pc, collects private knowledge, or tries to control your laptop in order that laptop hackers can entry it.
In case your antivirus shows a notification of Trojan:Win32/Reqletter, there are recordsdata left over. These Trojan:Win32/Reqletter associated recordsdata needs to be deleted. Sadly, Antivirus typically solely partially succeeds in eradicating the stays of Trojan:Win32/Reqletter.
The Trojan:Win32/Reqletter virus is malicious code designed to contaminate a pc or community system, typically damaging, disrupting, or stealing knowledge. It could unfold from laptop to laptop and may even have an effect on total networks. Pc viruses may be unfold by downloads, detachable storage media equivalent to USB drives, and even e mail attachments. This malicious content material has grow to be more and more refined through the years, making it more and more troublesome for customers to detect and defend their techniques from assault. Numerous laptop viruses, every with its traits and capabilities, can have disastrous penalties for any system or system contaminated.
Customers want to grasp the dangers related to laptop viruses and take steps to guard their knowledge from these malicious intruders.
A pc virus is any malicious software program designed to contaminate computer systems, harm knowledge, or disrupt operations. Pc viruses can unfold by networks and detachable media (equivalent to USB drives). They will also be despatched as e mail attachments. Some viruses may even self-replicate and infect different computer systems with out human interplay. There are various forms of laptop viruses and different malicious software program, equivalent to worms, Trojans, and different types of malware. They’re typically designed to wreck or disrupt laptop techniques and networks, steal info, or corrupt knowledge. Viruses and different malware may be unfold by contaminated recordsdata and web sites, e mail attachments, and different types of executable code.
Pc viruses can unfold in a number of alternative ways, relying on the kind of virus and the safety settings of the system they infect. A lot malicious software program spreads by e mail, web sites, or different recordsdata. Electronic mail attachments are a typical approach for laptop viruses to unfold. They are often despatched as an e mail attachment or embedded within the e mail message itself. If an e mail attachment is contaminated, it could infect the system it’s opened and some other units that the contaminated attachment is copied to. Pc viruses also can unfold by web sites that host malicious software program, equivalent to social media websites that distribute faux movies, pictures, and different content material. Web sites also can host malicious code, which might infect a tool if a person clicks on a hyperlink or visits the location.
The signs of an an infection rely closely on the kind of virus that has contaminated a tool. Normal signs of an an infection embrace the next:
- A pc that’s working extra slowly than regular
- A considerable amount of knowledge being despatched or obtained
- A pc that’s excessively utilizing its reminiscence or processor
- A lot of pop-up ads
- A pc that runs packages routinely when it’s not in use
- A considerable amount of knowledge being deleted from a pc
These signs might point out that a pc is contaminated with the Trojan:Win32/Reqletter virus. Customers might wish to scan the system for viruses if a pc is experiencing any of those signs. A pc virus scanner may help determine viruses and different malicious software program on a tool. It’s vital to notice that these scanners aren’t all the time utterly correct, so customers ought to take a number of steps to verify the outcomes. Customers might wish to take steps to scrub the system if a pc is contaminated with a pc virus.
Pc viruses can have a variety of results on a pc and the person’s knowledge. They’ll disrupt operations, harm knowledge, or render a pc unusable. Some laptop viruses also can unfold to different computer systems and networks, infecting many units concurrently. These sorts of viruses may be extraordinarily damaging and troublesome to take away. In some instances, buying new units or restoring knowledge from a backup could also be essential to take away the Trojan:Win32/Reqletter virus absolutely. The dangers of laptop viruses are quite a few, and customers have to take steps to guard their units from an infection.
Detecting the Trojan:Win32/Reqletter laptop virus is usually a troublesome course of. Customers ought to recurrently verify their units for viruses, as it could be troublesome to detect an an infection whereas it’s occurring. Customers can verify their units with antivirus software program to see if they’ve any viruses. Comply with the directions under.
The way to take away Trojan:Win32/Reqletter
Malwarebytes anti-malware is an important software within the struggle in opposition to malware. Malwarebytes can take away many forms of Trojan:Win32/Reqletter malware that different software program does typically miss. Malwarebytes is costing you completely nothing. When cleansing up an contaminated laptop, Malwarebytes has all the time been free, and I like to recommend it as an important software within the battle in opposition to malware.
Obtain Malwarebytes
Set up Malwarebytes, and observe the on-screen directions.
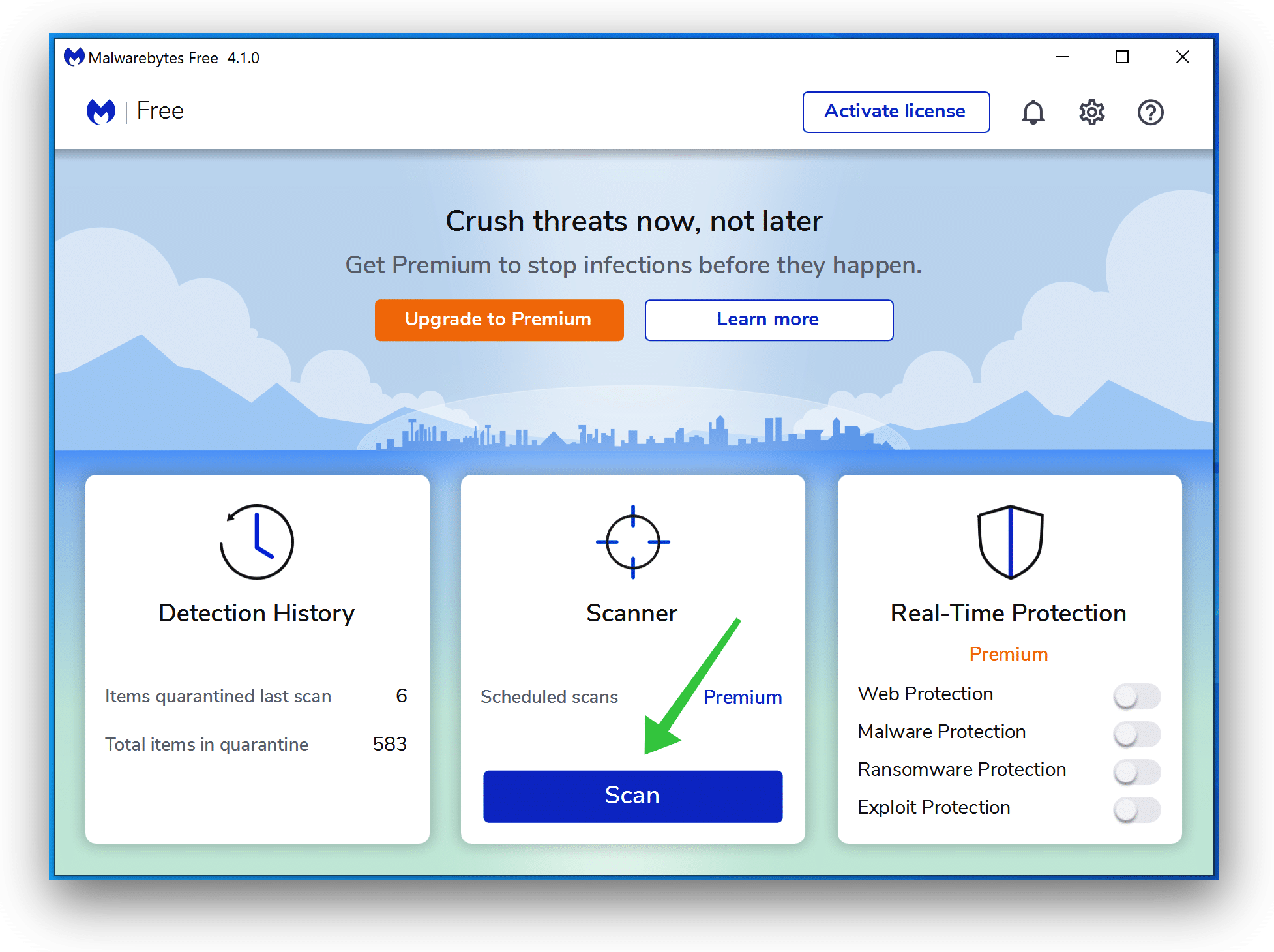
Click on Scan to begin a malware scan.
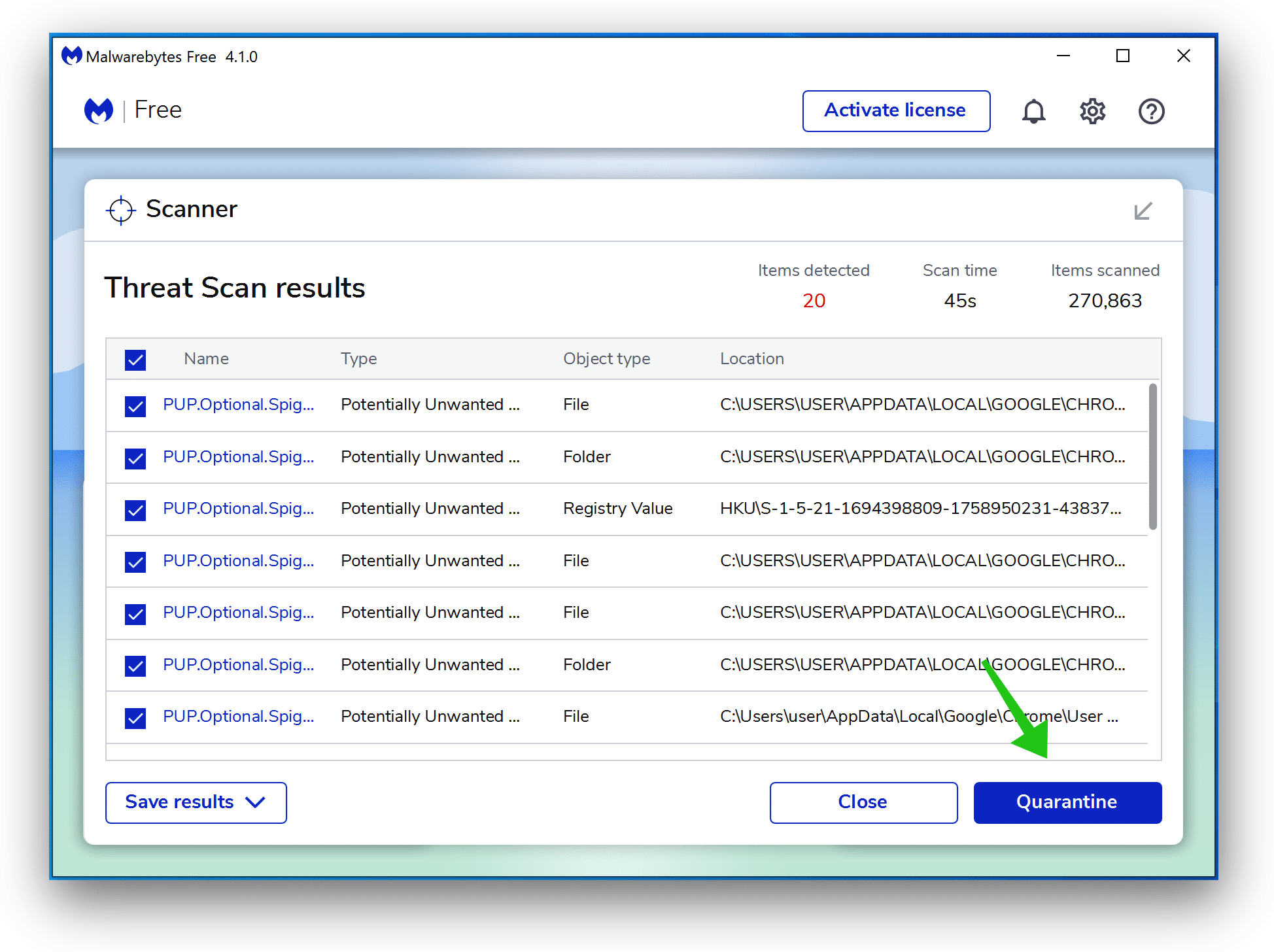
Anticipate the Malwarebytes scan to complete. As soon as accomplished, assessment the Trojan:Win32/Reqletter adware detections.
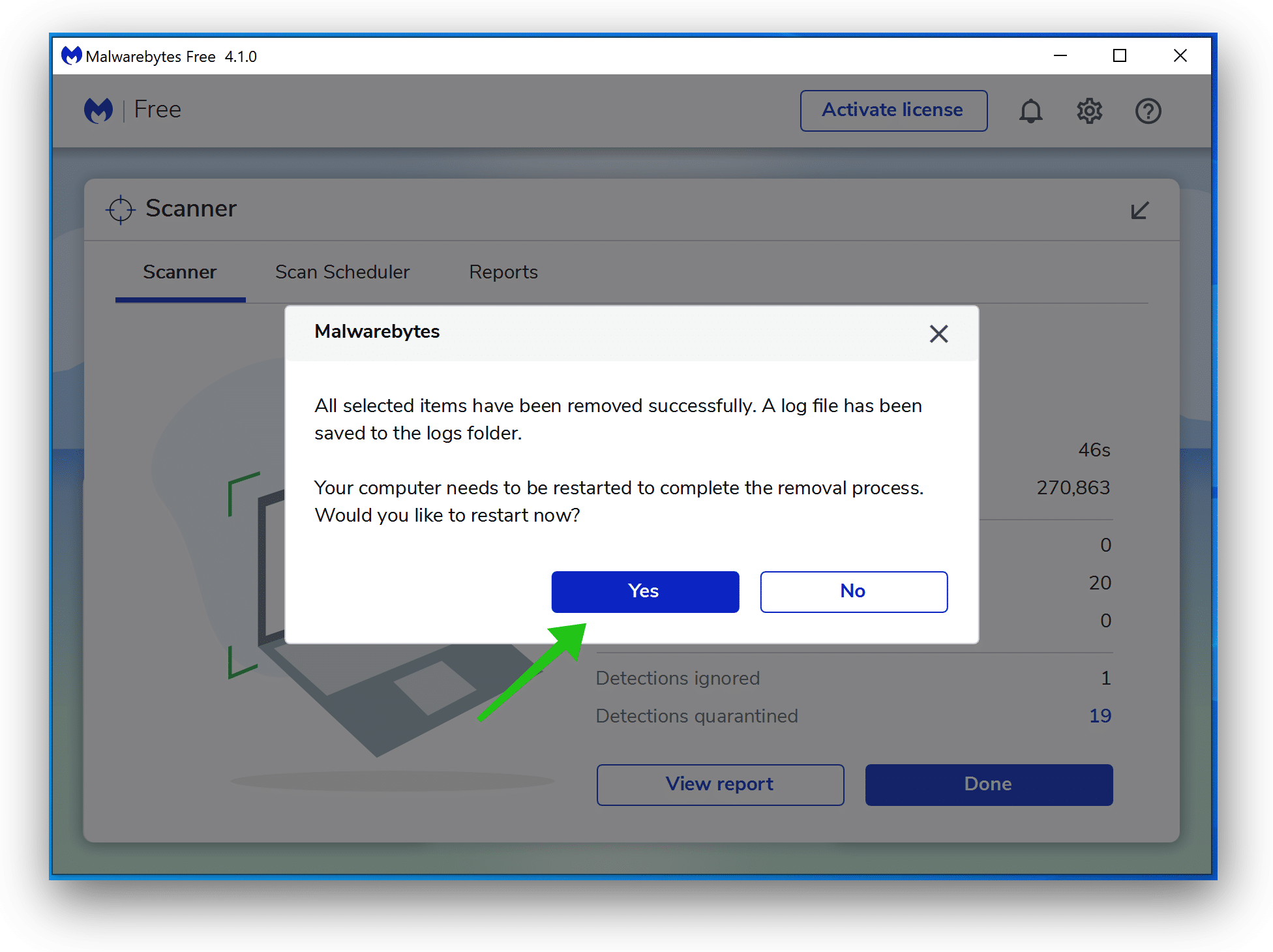
Click on Quarantine to proceed.
Reboot Home windows after all of the adware detections are moved to quarantine.
Proceed to the following step.
Take away undesirable packages with Sophos HitmanPRO
On this second malware elimination step, we are going to begin a second scan to make sure no malware remnants are left in your laptop. HitmanPRO is a cloud scanner that scans each lively file for malicious exercise in your laptop and sends it to the Sophos cloud for detection. Within the Sophos cloud, each Bitdefender antivirus and Kaspersky antivirus scan the file for malicious actions.
Obtain HitmanPRO
When you will have downloaded HitmanPRO set up the HitmanPro 32-bit or HitmanPRO x64. Downloads are saved to the Downloads folder in your laptop.
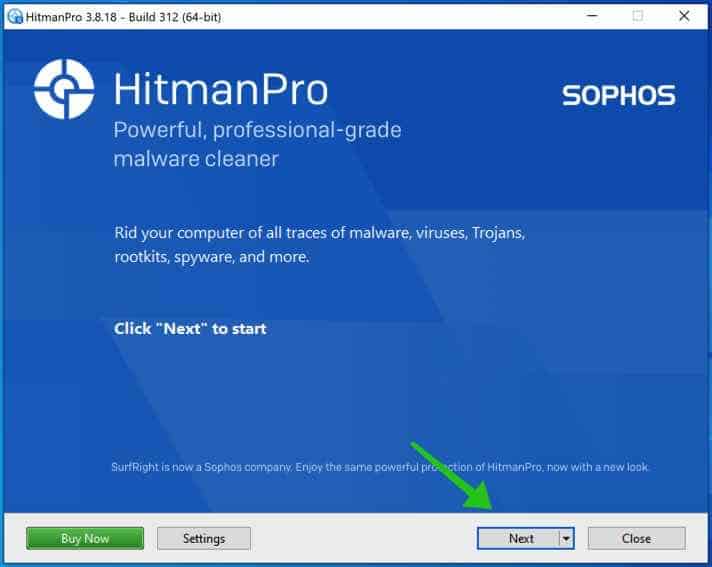
Open HitmanPRO to begin set up and scan.
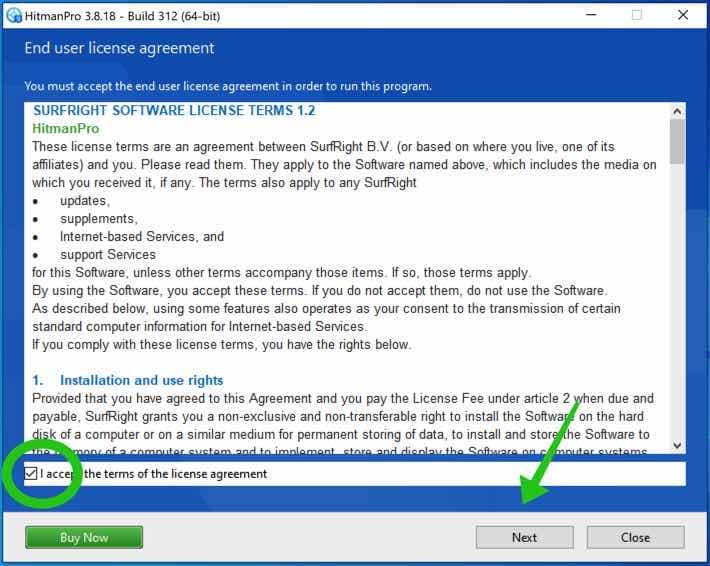
Settle for the Sophos HitmanPRO license settlement to proceed. Learn the license settlement, verify the field, and click on on Subsequent.
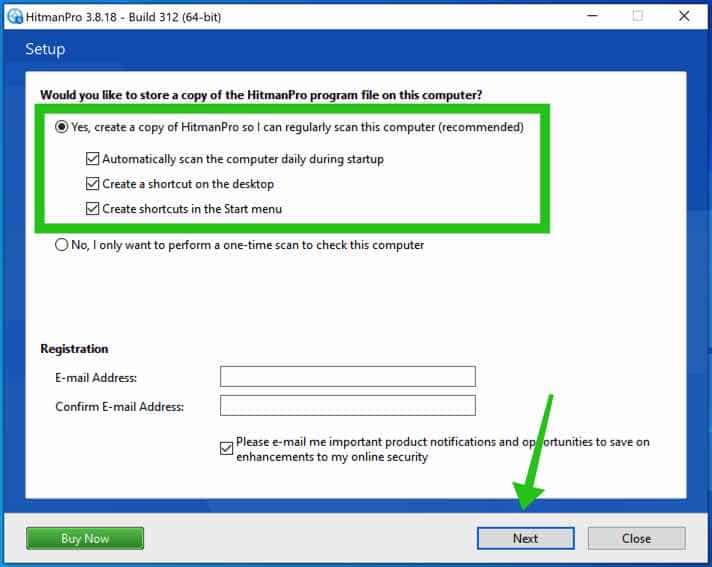
Click on the Subsequent button to proceed Sophos HitmanPRO set up. Be certain to create a replica of HitmanPRO for normal scans.
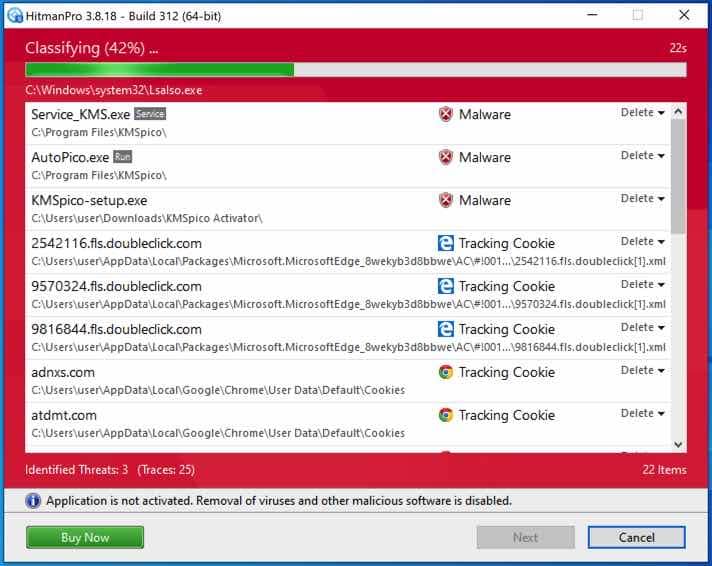
HitmanPRO begins with a scan, look ahead to the antivirus scan outcomes.
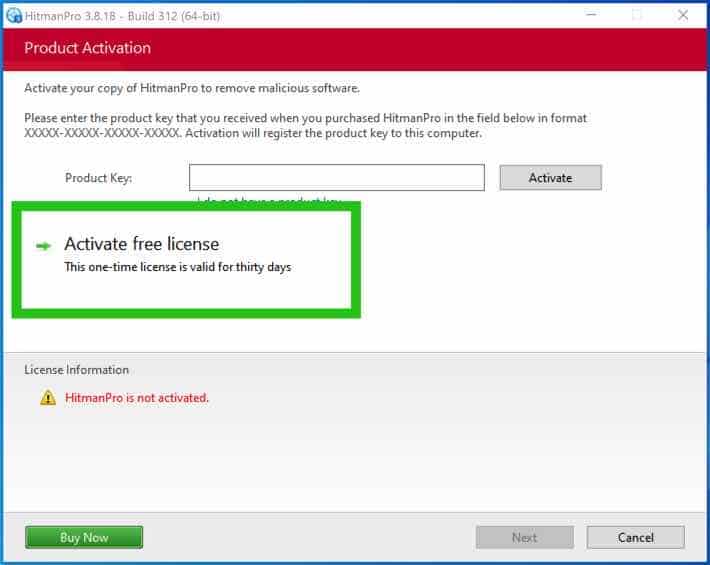
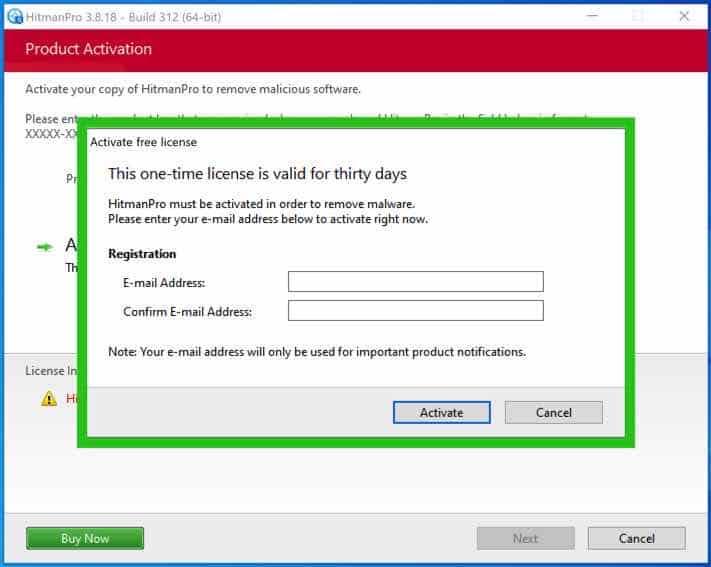
When the scan is finished, click on Subsequent and activate the free HitmanPRO license. Click on on Activate Free license.
Enter your e-mail for a Sophos HitmanPRO free thirty days license. Click on on Activate.
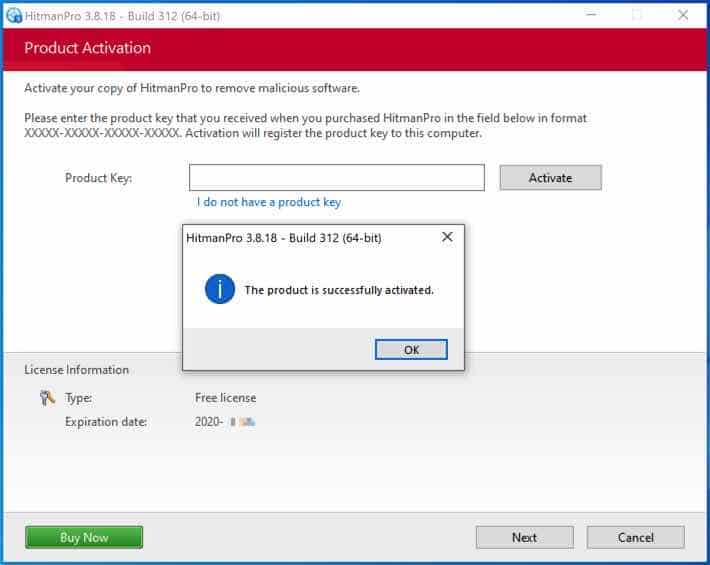
The free HitmanPRO license is efficiently activated.
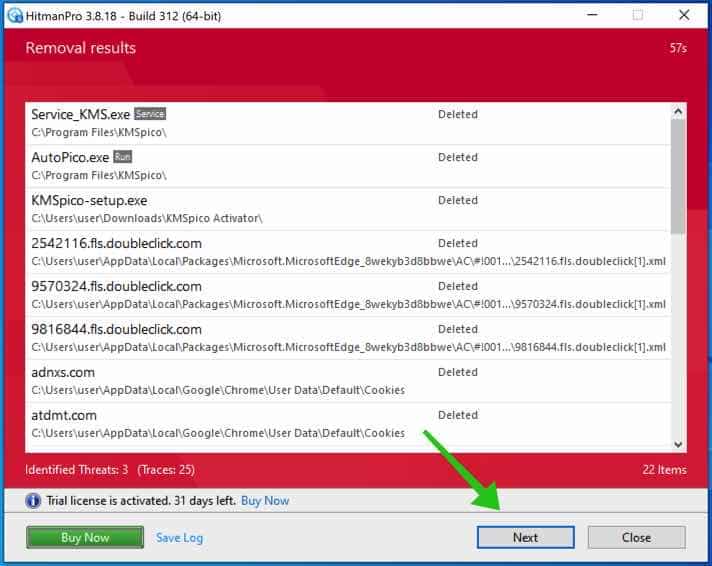
You’ll be introduced with the malware elimination outcomes. Click on Subsequent to proceed.
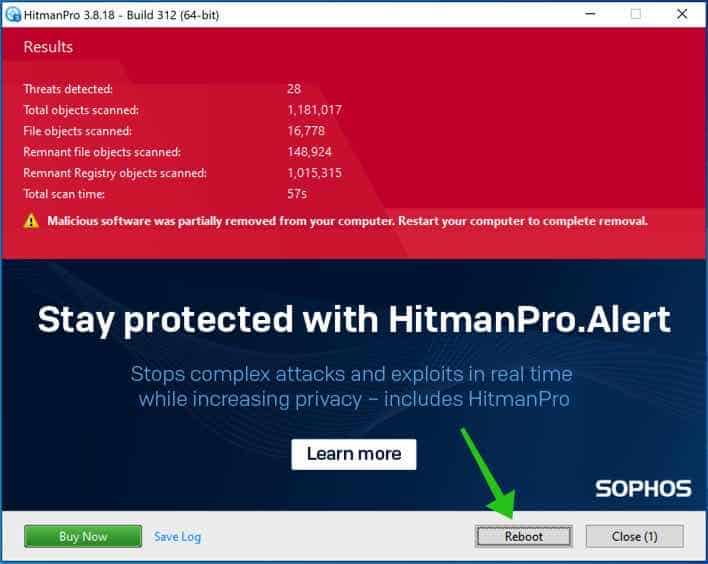
Malicious software program was partially eliminated out of your laptop. Restart your laptop to finish the elimination.
Bookmark this web page once you reboot your laptop.
The way to forestall Trojan:Win32/Reqletter virus?
One of the best ways to forestall the Trojan:Win32/Reqletter virus is to put in antivirus software program on each system, equivalent to Malwarebytes. It’s additionally vital to maintain all units linked to a community up-to-date with the most recent software program patches and safety updates. Customers also needs to keep away from clicking on hyperlinks inside emails from unknown senders, downloading recordsdata from unknown web sites, or visiting web sites which might be identified to distribute viruses or malicious software program.
Customers also needs to keep away from opening e mail attachments except they’re anticipating them. If a hyperlink or e mail attachment is predicted, customers ought to scan it with antivirus software program earlier than opening it. Customers also needs to watch out about what units they plug into their community and what detachable media they use to switch knowledge between units. It’s vital to notice that no system is 100% resistant to viruses. Even units with antivirus software program put in can grow to be contaminated with a pc virus.
Customers can observe a number of finest practices to guard themselves in opposition to laptop viruses. These embrace the next:
- Preserve all units up-to-date with the most recent software program updates.
- Use antivirus software program on all units.
- Scan all hyperlinks, recordsdata, and e mail attachments earlier than opening them.
- Keep away from clicking on hyperlinks from unknown senders.
- Keep away from downloading recordsdata from unknown web sites.
- Keep away from visiting web sites which might be identified to distribute viruses or malicious software program.
- Watch out about what units you plug into your community.
- Watch out about what detachable media you employ to switch knowledge between units.
- Commonly verify your units for viruses.
I hope this helped. Thanks for studying!